VPN(Virtual Private Networking): Difference between revisions
(Uus lehekülg: 'This page is not a tutorial on OpenVPN or on IPsec. It gives general overview of different setups and shows options found from configuration software gws.exe. It is assumed that ...') |
No edit summary |
||
| Line 1: | Line 1: | ||
This page is not a tutorial on OpenVPN or on IPsec. It gives general overview of different setups and shows options found from configuration software gws.exe. It is assumed that reader is familiar with TELEM-GWM configuration software gws.exe and understands how to secure the device. Securing the device is described in [[Basic Security]]. | This page is not a tutorial on OpenVPN or on IPsec. It gives general overview of different setups and shows options found from configuration software gws.exe. It is assumed that reader is familiar with TELEM-GWM configuration software gws.exe and understands how to secure the device. Securing the device is described in [[Basic Security]]. | ||
=== VPN Setups === | |||
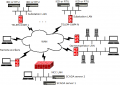
We have two typical configuration possibilities: site to site and remote access. Site to site is more suited when persistent connectivity is needed. For instance from RTU to Network Control Center(NCC). Remote access is provided for cases when non persistent access is needed or when persistent tunnel is not needed. For example remote management(configuration changes or etc) from different locations with dynamic IP address. Figure 1 illustrates this general concept. | |||
<gallery> | |||
image:vpn.png|right|thumb|500px|Figure 1: General Model for VPN Deploiments | |||
</gallery> | |||
Revision as of 06:15, 27 May 2013
This page is not a tutorial on OpenVPN or on IPsec. It gives general overview of different setups and shows options found from configuration software gws.exe. It is assumed that reader is familiar with TELEM-GWM configuration software gws.exe and understands how to secure the device. Securing the device is described in Basic Security.
VPN Setups
We have two typical configuration possibilities: site to site and remote access. Site to site is more suited when persistent connectivity is needed. For instance from RTU to Network Control Center(NCC). Remote access is provided for cases when non persistent access is needed or when persistent tunnel is not needed. For example remote management(configuration changes or etc) from different locations with dynamic IP address. Figure 1 illustrates this general concept.